SF State BuyIT requests, whether purchased or free, are required to be reviewed for operational support, accessibility, and information security requirements prior to acquisition and use.
All technology purchases require the BuyIt process to be completed before approving the acquisition. In the case of pre-approved technology, the required BuyIT process has already occurred.
Services involving an IT component, such as consulting services requiring access to the University systems and/or data, also require a BuyIT process to be completed.
The BuyIt process is used to (1) reduce IT costs by leveraging existing technology purchases and contracts; (2) determine whether the technology meets CSU/ campus standards (3) meet compliance requirements with CSU policies and SF State practice directives, e.g., accessibility and IT security which helps to reduce the risk of data breaches resulting in harm to CSU or individuals and any damages arising out of these breaches, and (4) ensure campus resources are available to support the chosen technology.
The longtime campus Technology Acquisition Request (TAR) process was officially relaunched in summer 2024! We are thrilled to introduce a new streamlined interface and process under a new name: BuyIT.
As part of a California State University requirement, SF State technology acquisitions, whether purchased or free, must be reviewed prior to acquisition and use for operational support, accessibility, and information security requirements.
After an extensive assessment of the process and its requirements, including user focus group feedback sessions, the project team developed an application to support the new IT purchasing process. The new application provides a consistent and simplified experience that is intended to get even easier as we streamline application functionality.
This change was part of a year-long collaborative effort between Academic Technology (AT), Information Technology Services (ITS), and other campus partners, including Procurement and the Disability Programs and Resource Center (DPRC). We also benefitted from campus input through focus groups and a staff and faculty user group whose input has been critical to this process improvement initiative.
How does IT purchasing work?
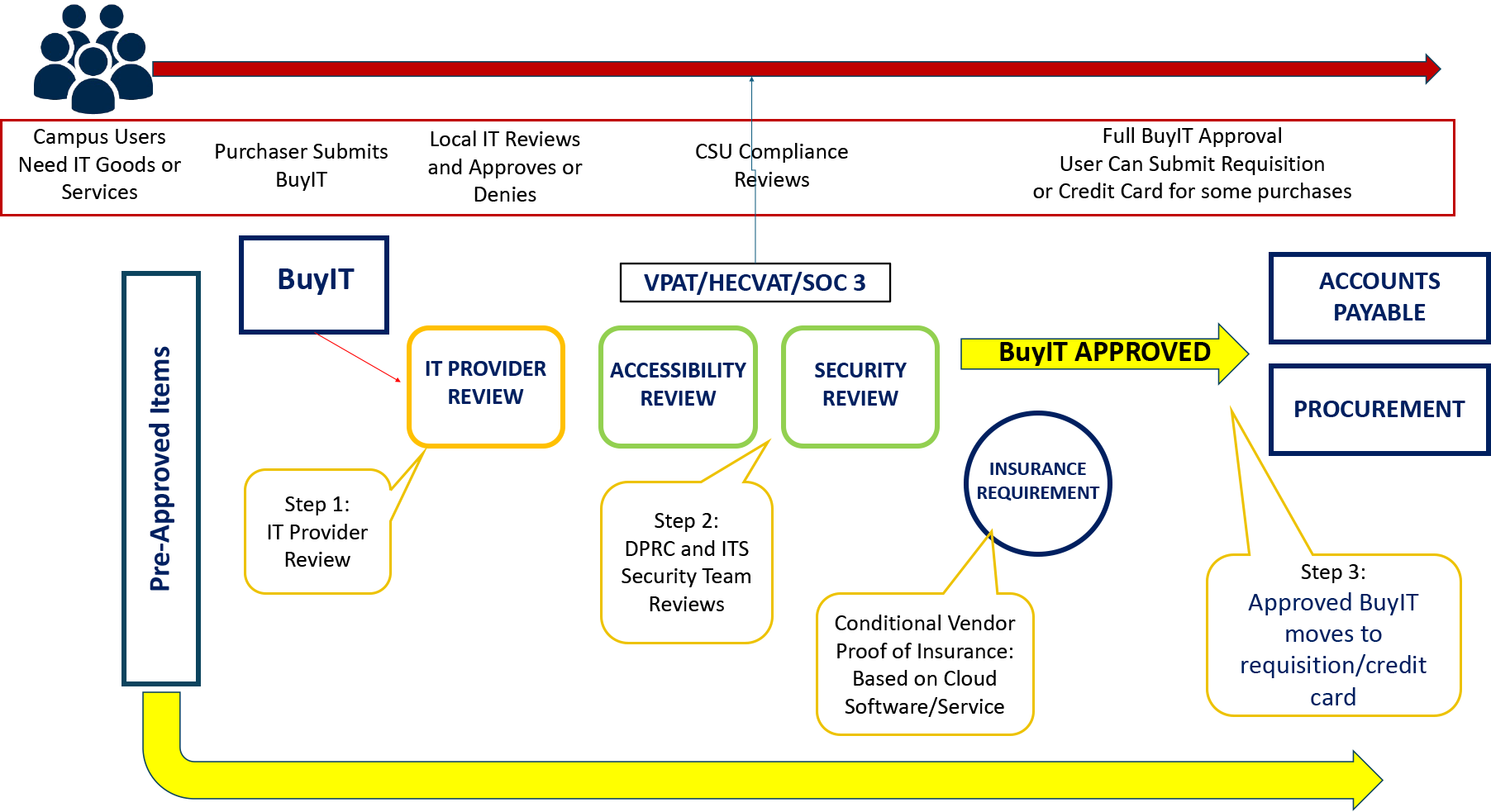
Phase 1: Campus IT Support Team Review
- Support and service level models needed
- Integrations
- IT process alignment
- Identifying potential redundant technology
- Identification of timing constraints, if applicable
If Campus IT Support does not approve the BuyIT request, the acquisition may not proceed until approval is granted.
Phase 2: Accessible Technology Review
If the request does not pass the accessibility review, the acquisition will not move forward.
Voluntary Product Accessibility Template (VPAT)
A VPAT, or Voluntary Product Accessibility Template, is a self-assessment document completed by a vendor that provides relevant information on how their product or service claims to conform to Accessibility Standards.
Phase 3: Information Security Team Review
- Indicate additional compensating controls, if needed, and determine if supplemental IT contractual terms are necessary.
The acquisition will not move forward if the request does not pass the security review.
Cloud Computing Acquisitions Documents
The vendor will be asked to provide one of the following cloud security assessment documents:
- A current SSAE-16 SOC 2 Type II (or equivalent third-party audited security standard).
- A current Cloud Security Alliance Consensus Assessment Initiative Questionnaire (CSA CAIQ).
- An industry-recognized current security certification or accreditation (e.g., FedRAMP authorized, ISO270xx, etc.).
- The Higher Education Cloud Vendor Assessment Tool (HECVAT).
Based upon the type of data being stored in the cloud solution, only one of the following documents identified in the table below is necessary to meet the requirement.
| Type | Data Classification | Type of Documentation Accepted | ||||
|---|---|---|---|---|---|---|
| Soc2 Type2 | ISO 270xx Certification | FEDRAMP Authorized | HECVAT Full | HECTVAT Lite | Other CSA CAIQ, or BuyIt questionnaire | |
| Level 1 | x | x | x | x | x | |
| Level 2 – high record count | x | x | x | x | x | |
| Level 2 – small record count | x | x | x | x | x | |
| Public | x | x | x | x |
For more information, see:
ICSUAM 8065.S003 Information Security Asset Management – Cloud Storage & Services
Risk Acceptance Form
A risk acceptance form is used to document non-compliance with CSU policy. The form lists any mitigating controls that are used to reduce the risk, and indicates when the risk will be remediated or next reviewed. An administrator capable of assuming the risk and the Information Security Officer must approve the risk acceptance. The Information Security team can assist with preparing the form.
Contracts
Supplemental IT contractual terms are CSU boilerplate contractual language that addresses information security risks and can be tailored to the technology acquisition scope. The Information Security team determines if the acquisition requires any supplemental IT contractual terms to protect CSU liability. In most cases, supplemental IT contractual terms are not necessary for hardware purchases. In many cases, they are required for cloud services, software, and other IT services.
When supplemental IT contractual terms are identified for an acquisition, the term numbers should be forwarded to Procurement and Support Services so they can be included and/or negotiated with the vendor.
If you have already submitted a requisition, forward the approved BuyIt request to Procurement and identify the supplemental IT contractual term numbers that were provided in your approved BuyIt request. If you have not submitted a requisition, include the approved BuyIT request and supplemental IT contract term numbers in the comment section when you submit your requisition.
Phase 4: Completion and Approval
When Phases 1, 2, and 3 have been completed and approved, the requesting department submits a requisition to the Procurement department with the BuyIT approval letter and other pertinent information. The letter must be submitted at the time of the Pcard reconciliation. Pcard use is only allowed for purchases under the direction of Procurement.